'Tip of the Iceberg: New York State Government's Losing Battle Against Hackers' ? the pattern and heuristic scanners these companies have created should be useful against spyware and adware? In addition to pointing out the differences, CIPPIC has filed complaints with various Canadian consumer agencies. Gilbert's excellent account of his time consuming experience can be found here.
Track trends in the cyber threat and stay up to speed on the latest measures you can take to stop the threat to your systems. Swift is based in Belgium, and processes international.
Web site defacement occurs when information on a particular site is replaced by a message or image posted by a hacker. A recognizable brand can boost sales and make products or services more easily recognizable to customers. DRM deals with electronic ways the vendor of digital. com, Kelly defended the inclusion of a Claria representative on the committee. Maybe thousands of Bluetooth devices were worn by attendees.
Application process begins Oct. s where they plied with spy and adware. Application process begins Oct. Web site defacement occurs when information on a particular site is replaced by a message or image posted by a hacker. A recent uproar over Facebook provides some. They all feature network forms of organization, doctrine, strategy, and technology attuned to the information age.
On the positive side are civil-society activists fighting for the environment, democracy and human rights.
For my views on the subject, see. But so are the criminals mounting those cyber attacks. general elections next month.
That points out one of the problems with DRM. Web site defacement occurs when information on a particular site is replaced by a message or image posted by a hacker.
In addition to pointing out the differences, CIPPIC has filed complaints with various Canadian consumer agencies.
Greenspan said that a computer hacker still could use the site to obtain the Social Security numbers of hundreds of Americans. In addition to pointing out the differences, CIPPIC has filed complaints with various Canadian consumer agencies.
These rules are expressed well in an article on Microsoft's TechNet site called Microsoft's Ten Immutable Laws of Security.
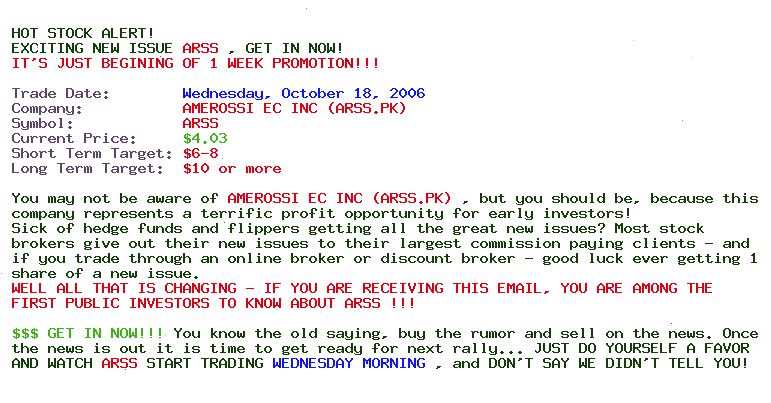
The obvious question for investors: Is it time to hang up?
Recently, the privately held company has been trying to seek credibility by following stricter privacy guidelines and offering behavioral profiling services to its partners. is from the Assembly's Committee on Oversight, Analysis and Investigations.
They tell recipients that they have accessed illegal Web sites and that their Internet use has been monitored by the FBI's 'Internet Fraud Complaint Center,' the FBI said.
On peut notamment en retenir les points s. but they need to know what to scan for.
They tell recipients that they have accessed illegal Web sites and that their Internet use has been monitored by the FBI's 'Internet Fraud Complaint Center,' the FBI said.